 |
As global companies increasingly rely on e-business to gain competitive advantage, they are more and more relying on networked supply-chain management and Internet trading communities that offer manufacturers efficient means to build an extended enterprise. Because sensitive, business-critical information flows through VPNs in and out of the corporate network, gateway security at the central data center level, as well as network perimeters, is required to prevent harmful virus, worm and intrusion attacks. A complicated network that global company operates, contains multiple devices from multiple vendors, this requires a total management in terms of controlling policy, managing auditing requirements, collecting status report from various devices. |
|
Firewalls
Firewalls are the cornerstone of policy enforcement in the enterprise network. i-Security
offers a wide range of products from the multi-gigabit SP-5500 to the compact SP-2000, with all products offering virtually the same functionality and user interface. Once again, when a user is trained to operate a i-Security SP series firewall, they are able to operate any other product in the family equally well.
Virtual Private Networks
Currently there are two varieties of VPNs that provide data confidentiality (encryption). IPSec VPN functionality is a standard component of all i-Security firewalls. SSL (Secure Sockets Layer) VPN functionality is provided by i-Security Connectra line of products which is considered to be a secure internet access technology. Only IPSec and SSL provide data confidentiality, authentication and data integrity using cryptographically secure methods.
Policy Management
Ensuring the highest levels of network protection and continuity of operation necessitates daily vigilance and constant updates – a task that is rendered difficult in the absence of centralized management tools.
i-Security’s solutions offer pragmatic features and functionality enabling enterprises to be proactive about their network security. Complexity of security rules: The definition and implementation of network security is particularly difficult in large manufacturers, where administrators need to provide different levels of security according to different users: while administrators require an open access to the Internet, labs and research servers need to be tightly protected against potential intrusions, production networks requires even stringent network protections.
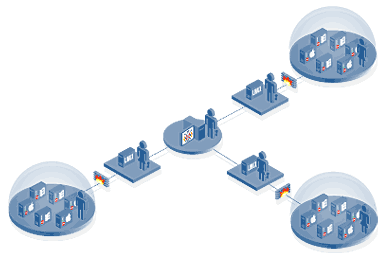
Diagram: Multiple administrator managing complicated network comprised of heterogeneous systems, devices and networks. |
|